“The risk of a wrong decision is preferable to the terror of indecision.”
― Maimonides, The Guide for the Perplexed
What’s the biggest risk in your project right now?
If your answer is something obvious—missed deadlines, budget overruns, or client dissatisfaction—you might not be thinking broadly enough. The biggest risks aren’t always the ones that make it to the meeting agenda. They hide in plain view—the ones your team doesn’t talk about until they’re already causing damage.
Imagine you are leading a major product launch, and every project milestone is carefully mapped out. Marketing has its campaign timeline, engineering has its development sprints, and sales is gearing up for outreach. On paper, everything looks airtight. But here’s what’s missing from your plan:
- A software update that isn’t compatible with existing tools, causing workflow disruptions
- A team member with key expertise unexpectedly leaving mid-project
- A misunderstood client requirement leading to costly revisions late in the project
Years ago, while developing ProofHub and managing several cross-functional initiatives, our team thought we had identified every conceivable risk—or so we assumed. Truth be told, our risk management was scattered across emails and informal meeting notes rather than a structured system. It wasn’t until a major deliverable slipped by three weeks that we realized what we were missing: a proper risk register.
You’re likely familiar with risk registers as a project management tool. Perhaps you’ve even created basic versions for compliance purposes or used templates provided by your organization. What many project managers discover, though, is that there’s a substantial difference between having a risk register and having one that prevents project derailment.
An effective risk register ensures that you don’t just react to problems—you anticipate them, and handle them proactively.
In this guide, I’ll explain how to build one that works, and the overlooked benefits that extend far beyond risk management to strengthen your overall project leadership approach. I will also discuss some of the prioritization techniques and integration approaches that keep risk management alive and effective throughout your projects.
What is a risk register?
A risk register is a structured document used in project management and organizational risk management to handle any potential risks that could impact objectives systematically.
At its core, a risk register is a structured tool that:
- Identifies risks (known and overlooked),
- Prioritizes them based on their likelihood and impact,
- Systematizes how teams respond to and monitor those risks over time.
Regardless of the scale and complexity of your project, risk management does not happen in isolation. You might already know how to spot risks using a risk matrix or how to rank them as “high” or “low.”
But most projects are dynamic. They undergo a lifecycle that is not necessarily linear. Hence, risks evolve.
- A “low-probability” risk gains momentum when three teams unknowingly make conflicting decisions.
- A “moderate-impact” risk can grow because no one revisited its assumptions after they found a momentous solution.
- A “closed” risk resurfaces months later in a different department.
These situations don’t come as complete surprises. More often, they come from sensed risks but never given enough weight.
Moreover, most teams often misrepresent the true impact of a risk. In fact, Louis Anthony Cox has conducted a remarkable study highlighting how traditional risk categorization methods can sometimes prioritize the wrong threats, making a risk seem bigger or smaller than it actually is. This means your team might be preparing for the wrong problems while ignoring the real threats.
A risk register systematically closes this gap between uncertainty and action. While a matrix answers “How bad is this today?”, a register answers:
- How do these risks interact over time?
- Who owns the response when priorities change?
- What assumptions are we betting on—and how do we validate them?
Convert hidden risks into visible action items. Start your 14-day ProofHub free trial.
Key benefits of using a risk register
What distinguishes a true risk register from a performative exercise is its integration into your project progress. It’s not merely a document you create during planning and reference when disaster strikes. A risk register transforms risk management from a reactive scramble into a proactive discipline where potential issues are anticipated, monitored, and addressed before they escalate.
- Strategic planning: Risk registers change your approach from reactive to proactive. Instead of scrambling when issues arise, you’ve already mapped potential problems and planned responses.
- Risk prioritization: Ranks risks by impact and likelihood, ensuring teams focus on what matters most. Beyond simple categorization, this gives veteran managers the insight to allocate precious resources where they’ll yield the greatest protection against genuine threats.
- Continuous learning: Your risk register becomes a valuable historical record over time. You’ll spot recurring issues across different projects that others miss. The moment when you identify a familiar risk pattern from three projects ago, your experience turns into actionable insight.
- Improve stakeholder alignment: When you present a comprehensive and transparent risk register to executives and clients, you demonstrate command of the project landscape. They see not just that you’ve identified potential problems but that you’ve thoughtfully prepared solutions. This builds trust far more effectively than reassurances alone.
- Better resource allocation: A detailed risk register transforms vague concerns into specific, quantified impacts, helping you plan a better budget for contingencies. When you can show precisely how and why resources are needed, you’re much more likely to secure them than managers who rely on general warnings.
- Team accountability: Assigning risk ownership creates clear responsibility without micromanagement. When team members see their names beside specific risks, they take ownership naturally, resulting in proactive problem-solving rather than waiting for direction.
Essential components of a risk register
Creating an effective risk register begins with the understanding that it serves as the central nervous system of project risk management—capturing, organizing, and facilitating the response to potential threats and opportunities. Organizations may use varying approaches or nomenclature, but the core elements remain consistent across industries and project sizes.
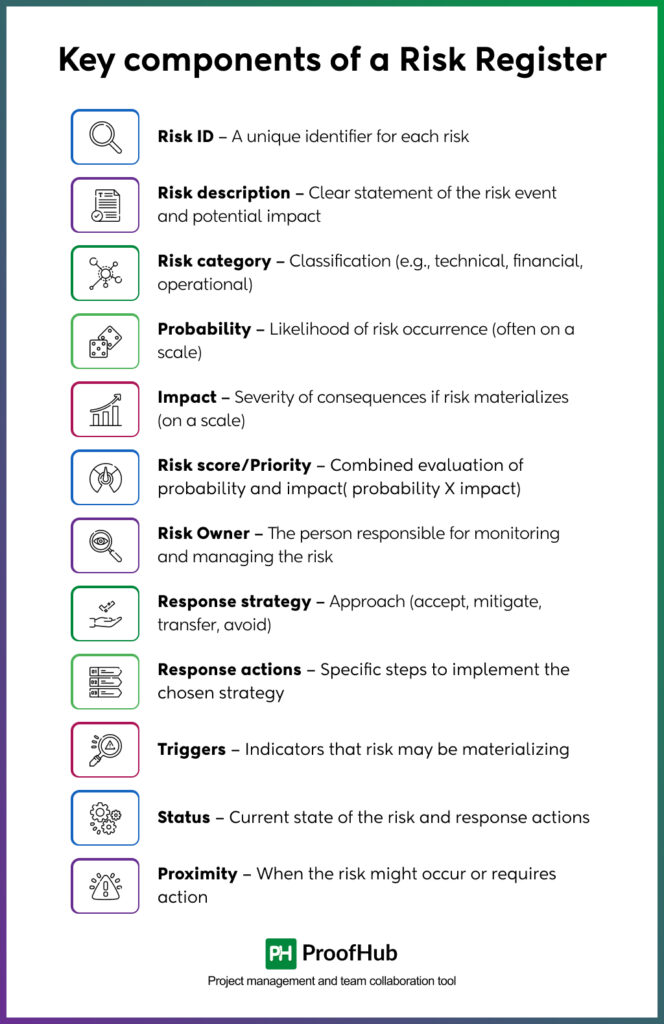
Key components of a risk register
- Risk ID – A unique identifier for each risk
- Risk description – Clear statement of the risk event and potential impact
- Risk category – Classification (e.g., technical, financial, operational)
- Probability – Likelihood of risk occurrence (often on a scale)
- Impact – Severity of consequences if risk materializes (on a scale)
- Risk score/Priority – Combined evaluation of probability and impact( probability X impact)
- Risk Owner – The person responsible for monitoring and managing the risk
- Response strategy – Approach (accept, mitigate, transfer, avoid)
- Response actions – Specific steps to implement the chosen strategy
- Triggers – Indicators that risk may be materializing
- Status – Current state of the risk and response actions
- Proximity– When the risk might occur or require action
I typically encourage my teams to first think broadly about categorizing risks into “knowns” and “unknowns.” In this context, known risks are those we can identify and anticipate based on experience or industry knowledge. In contrast, unknown risks represent areas of uncertainty where we lack complete information or where unprecedented events might occur. If you’re interested in exploring this classification system in greater depth, I recommend checking this article on modified risk classification frameworks that extend the traditional known-unknown matrix into more detailed categories that account for identification challenges and knowledge gaps.
Furthermore, the specific categorization system you choose should be tailored to your project’s unique characteristics. A software development project might benefit from technical/non-technical classifications, whereas a construction project might focus on internal/external risk sources. Ultimately, what matters isn’t the particular taxonomy but what that categorization accomplishes, i.e., creating a shared language for discussing risk, highlighting blind spots/bottlenecks, and ensuring comprehensive coverage across the project landscape.
To sum up, the purpose of any categorization system is ultimately to make the invisible visible. To ensure that risks aren’t missed simply because they fall outside our typical frames of reference. For example, NASA’s approach to International Space Station risk management demonstrates this principle beautifully. Their Continuous Risk Management (CRM) process uses tiered classifications (Concerns, Watch Items, and Risks) to capture uncertainties at different levels of definition and immediacy. This multi-level approach ensures that even vague or distant threats receive appropriate attention while maintaining focus on immediate risks requiring action.
Not every component listed above is absolutely necessary for every project. The scale and complexity of your undertaking should determine the sophistication of your risk register. What matters most is creating a living document that evolves with the project and facilitates meaningful risk conversations among stakeholders. With a solid understanding of these fundamental components, we can now explore how to create and maintain an effective risk register throughout the project lifecycle.
How to create an effective risk register? (with example)
Creating and managing a risk register might seem overwhelming, especially when you consider the various knowns, unknowns, and the ongoing nature of risk management. Earlier, project managers relied on spreadsheets that quickly became unwieldy, error-prone, and difficult to maintain.
Today, project management tools like ProofHub can do much of the heavy lifting, providing structure, organization, and collaborative features that convert risk management from a burden into a strategic advantage.
Step-by-step process to create a risk register
Different projects and organizations require different levels of detail and focus areas while creating a risk register. For simplicity, I’ll walk you through creating a simple yet effective risk register using ProofHub. Despite its straightforward nature, this exact register format had helped our teams discover hidden patterns that could later turn into huge risks. Here’s the step-by-step process for creating a risk register:
1. Risk identification
Teams often struggle with this crucial first step because they’re either too optimistic (“nothing will go wrong”) or overwhelmed (“everything could go wrong”). Here, you need a structured approach of honest assessment minus the panic.
Eventually, it comes to the leadership. A project manager who successfully establishes a culture where team members feel safe identifying potential problems makes risk identification a valuable opportunity rather than a dreaded exercise. The power of collective intelligence through brainstorming can’t be overstated, and stakeholder interviews often reveal concerns you might never have considered.
One method that has stood the test of time for me is RAID analysis:
- Risks: Potential problems
- Assumptions: Factors taken as true without proof
- Issues: Actual problems occurring now
- Dependencies: Reliance on external factors
It provides a structured approach to identify and manage these elements throughout a project’s lifecycle. Other methods include SWOT analysis, historical data analysis, etc.
In ProofHub:
- Create a dedicated “Risk Management” project to centralize all risk-related activities.
(If the complexity is not that high, you can just set up a task list within an existing project)
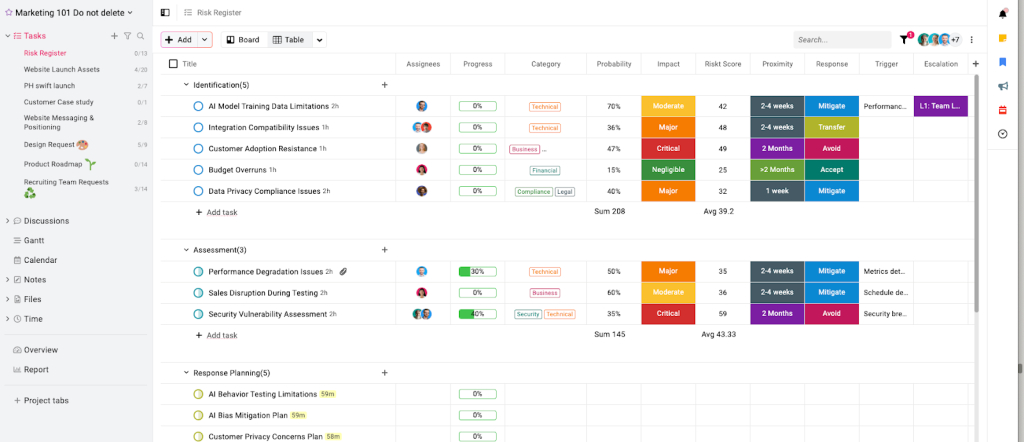
- Set up a simple “Risk planning/Identification” discussion board for team contributions
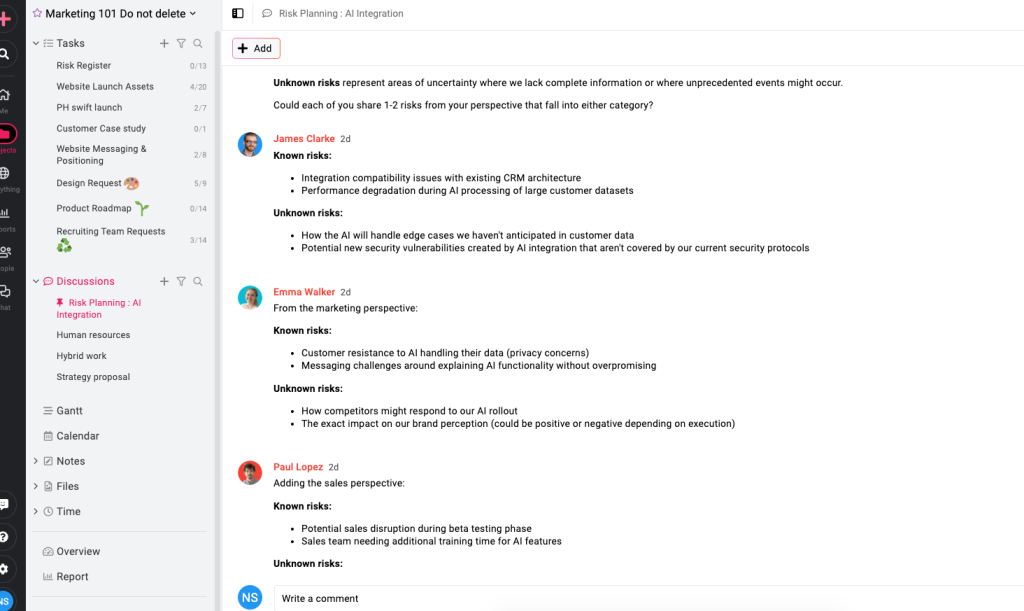
- Use the “Notes” feature to document outputs from your chosen identification methods
2. Risk categorization
Once risks are identified, categorization brings order to what might otherwise feel like an imminent collapse. Many projects derailed not because risks weren’t identified but because they weren’t properly organized. Effective categorization allows you to see patterns, allocate resources appropriately, and ensure nothing falls through the cracks.
Categories should be meaningful to your specific project and organization. While there are standard frameworks like internal/external or strategic/operational, the most effective categorization system is one that speaks the language of your team. It isn’t about academic perfection. You should create a system that makes sense to the people using it.
In ProofHub:
- You can create straightforward labels for broad categories
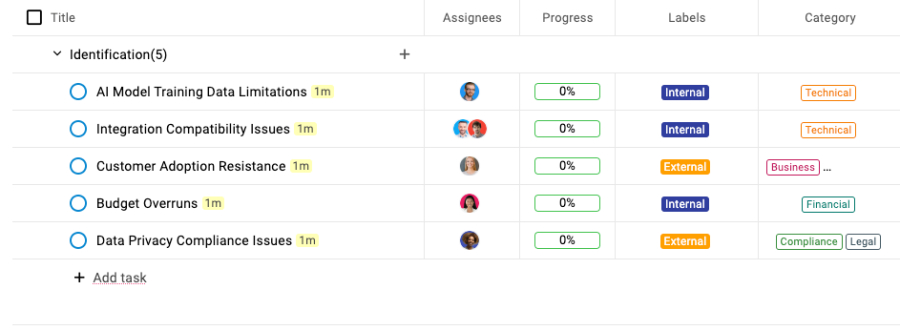
- Use custom fields for more specific categories that matter to your project
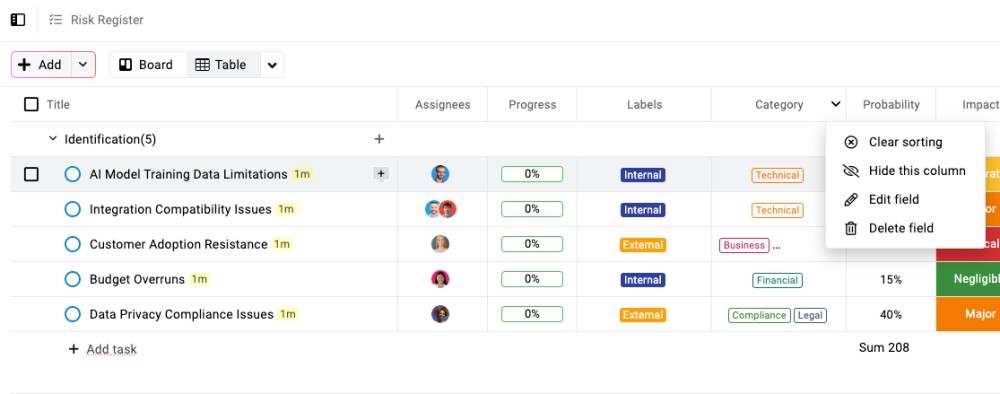
Pro tip: Keep the categorization simple enough that team members can quickly assign categories without overthinking
3. Risk analysis
Risk analysis is the process where your list of risks becomes a decision-making tool. It is commonly known that effective risk analysis combines both quantitative and qualitative approaches, each serving different but complementary purposes.
Quantitative risk analysis deals with concrete numbers—probability percentages, financial impact, and schedule delays in days or weeks. These metrics provide clarity and allow for precise prioritization. However, my experience tells me that not everything that matters can be measured, and not everything we can measure actually matters.
Qualitative risk analysis captures the nuances that numbers miss—reputational impact, team morale effects, and stakeholder perception. For these aspects, I recommend using defined scales with clear descriptors rather than vague labels. For example, complement “Low/Medium/High” for impact with triggers, proximity, or detailed description.
Also, one aspect that I have often found missing from most of the risk registers is the correlation between risks.
Risks rarely exist in isolation. They form networks where one triggering event can cascade through multiple risk areas. When analyzing risks, ask: “If this happens, what else might happen as a result?” This systems thinking approach often reveals vulnerabilities that isolated risk assessment misses.
Another crucial consideration is risk velocity (or proximity): how quickly a risk can impact your project after being triggered. Some risks unfold gradually, giving you time to implement contingency plans. Others hit like lightning, requiring immediate response.
In ProofHub
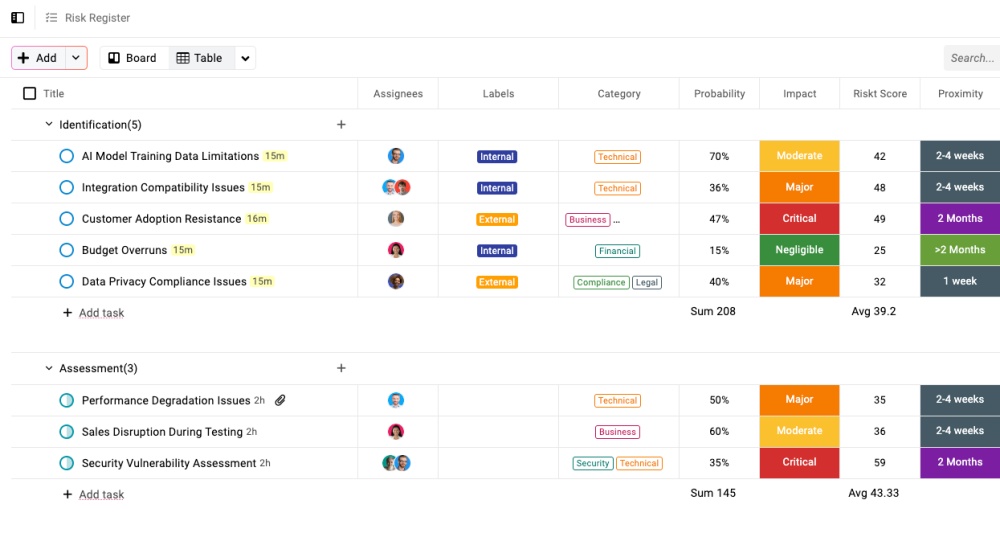
- Set up custom fields for quantitative measures and qualitative assessments
- Create a “Risk Score” field combining quantitative and qualitative factors
- Add a “Proximity” field (Immediate/Rapid/Moderate/Slow)
4. Response strategy development
Response strategy development brings a structural approach to risk management. The idea is fairly simple: assess, think, choose, and act.
Most teams, however, instinctively jump to mitigation. It’s comfortable, I get it, but not always optimal. Resources get wasted on mitigating minor risks while major threats loom unaddressed.
A strategic response selection requires both analytical rigor and creative thinking. The four classic strategies—avoid, mitigate, transfer, and accept—form a great toolkit.
- Avoidance eliminates the risk entirely, often through scope or approach changes.
- Mitigation reduces either probability or impact.
- Transfer shifts responsibility to a third party better equipped to handle it.
- Acceptance acknowledges the risk without immediate action.
Risk severity and appetite vary dramatically across organizations. I have worked with clients that avoid even modest risks (fin-tech types) and startups that embrace a significant level of uncertainty.
The most effective strategy often combines approaches. For technical risks, you might mitigate the highest-impact components while accepting minor elements. For market risks, you could transfer some aspects through partnerships while avoiding others through phased implementation.
In ProofHub:
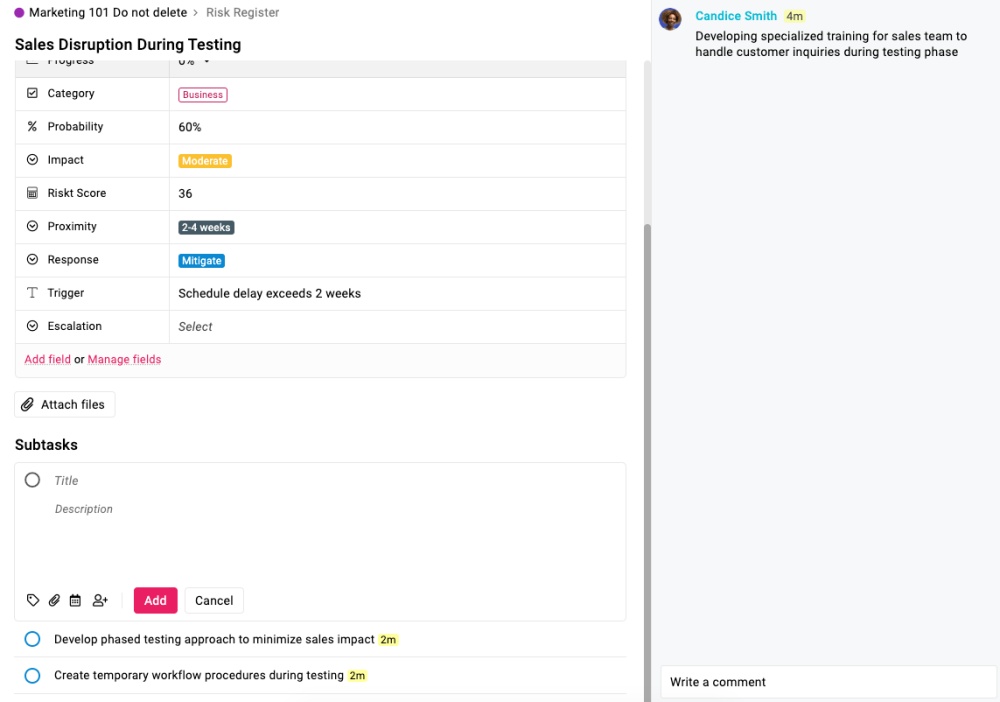
- Create a custom dropdown field for primary response strategies
- Build subtasks for concrete action steps
- Assign specific owners to each response action
- Set realistic implementation deadlines with a buffer for complications
5. Mitigation planning
Good intentions crumble without methodical implementation. Effective mitigation plans share three characteristics: specificity, measurability, and appropriate resourcing. Vague plans fail most of the time. Unmeasurable plans provide false confidence. Under-resourced plans create frustration and team burnout.
Resource constraints are inevitable. Accept them and prioritize accordingly. One fully implemented mitigation plan outperforms ten half-completed efforts. This requires honest capability assessment. Can your team actually execute what you’re planning? If not, reconsider your approach.
Mitigation plans should include checkpoints. These allow for course correction if initial efforts prove insufficient or circumstances change. Flexibility within the structure creates resilience.
In ProofHub:
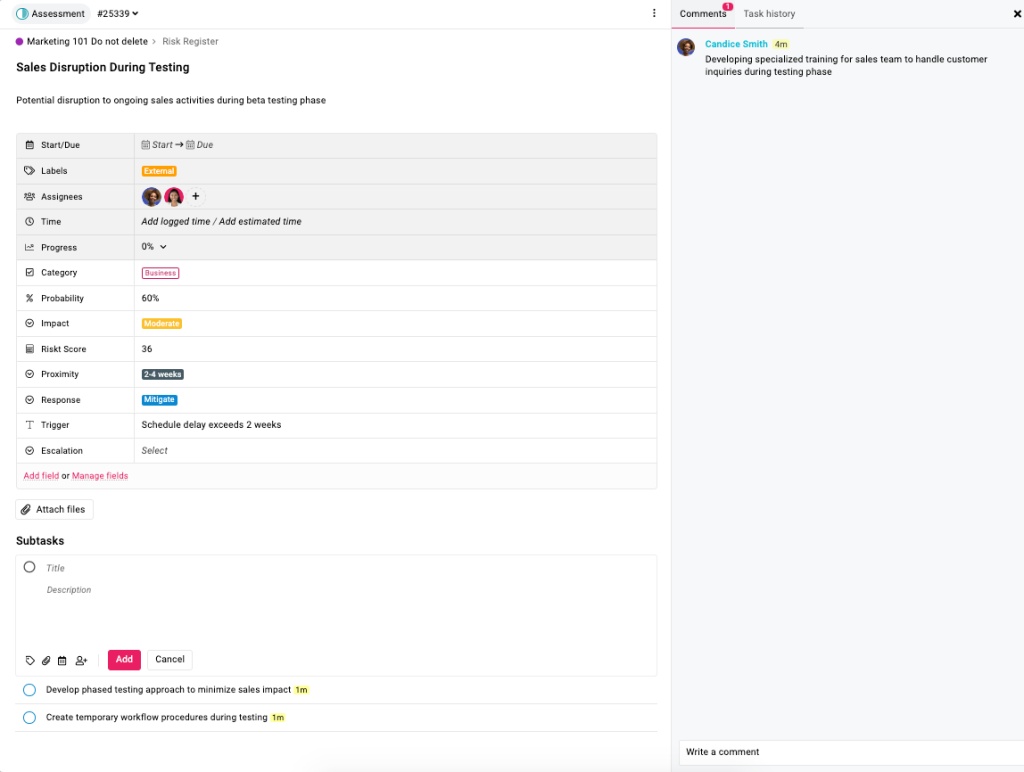
- Use the “Description” field for clear mitigation strategies
- Track progress
- Document resource requirements explicitly
- Include measurable success criteria for each mitigation action
- Attach only essential supporting documents to prevent information overload
6. Contingency planning
Contingency planning is for the risks to materialize despite your best efforts. It’s plan B, and the projects absolutely need one. Effective contingency plans require clear triggers, specific actions, and defined roles. Triggers eliminate dangerous delays in response initiation. Actions prevent decision paralysis during a crisis. Defined roles eliminate confusion about who does what.
The sweet spot for contingency planning is detailed guidance with flexible implementation. Too rigid, and plans break under pressure. They are too vague, and they provide insufficient direction. Aim for actionable principles rather than inflexible procedures.
I like to pre-approve contingency resources, which dramatically reduce response time. Projects save weeks by having emergency budget allocations or temporary staff arrangements prepared in advance. These preparations demonstrate strategic foresight to stakeholders.
Contingency planning also reveals organizational maturity. Immature organizations view contingency planning as a pessimistic approach. Mature organizations recognize it as ensuring success regardless of circumstances.
In ProofHub:
- Create a connected task hierarchy for contingency actions
- Implement clear task dependencies to guide the response sequence
- Document pre-approved contingency resources and their activation process
7. Monitoring and review
Monitoring and review transform risk management from a document into a discipline. A neglected risk register creates dangerous illusions of control.
Risks evolve. They emerge. They diminish. They transform. Your monitoring approach must match this dynamic reality. Schedule regular reviews—monthly or quarterly, depending on project velocity. Supplement these with trigger-based assessments when significant changes occur. The combination provides both discipline and adaptability. Focus on the following questions:
- Are your strategies working?
- Are they resource-efficient?
- Are they creating unintended consequences?
These questions reveal improvement opportunities. Data tells stories. Collect it systematically. The pattern of risk evolution across projects contains invaluable organizational learning. I’ve seen companies transform their project success rates simply by analyzing historical risk management data.
Risk reviews should be forward-looking, not blame-oriented. Create psychological safety for honest assessment. Teams that feel judged will hide problems until they’re unmanageable. Teams that feel supported will surface issues early when solutions are still possible.
In ProofHub:
- Configure recurring tasks for scheduled risk reviews
- Implement progress tracking to monitor risk evolution
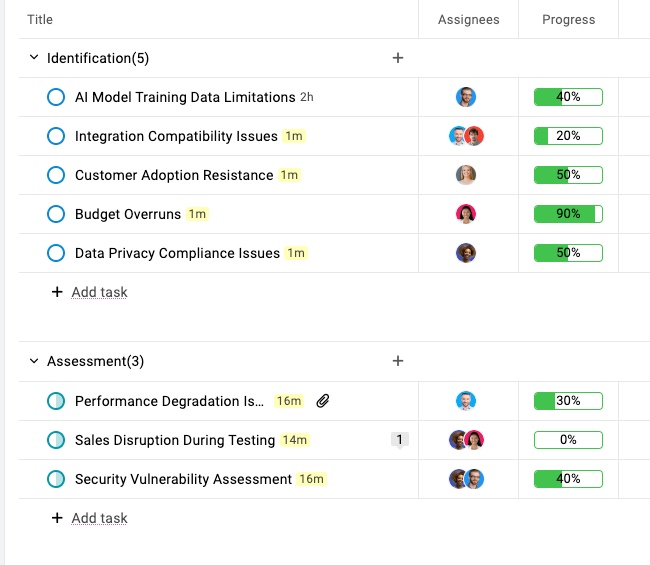
- Maintain a comprehensive activity log for audit and learning purposes
Rist register example log entry
Let me demonstrate how risk progresses through all seven steps with a concrete example:
- Risk ID: AI-207
- Risk description: AI system may produce biased recommendations for certain customer segments due to training data limitations
- Risk categorization:
- Primary category: Internal
- Secondary category: Ethical
- Risk analysis
- Probability: 3/5 (Medium) – Based on preliminary data analysis and industry patterns
- Impact: 4/5 (High) – Potential damage to customer relationships and brand reputation
- Risk score: 12/25 (High)
- Proximity: 2 months (May 2025)
- Response strategy
- Strategy: Mitigate
- Rationale (Comment): Cannot be completely avoided as bias detection is inherently challenging; transfer not feasible for core product functionality
- Mitigation actions (Subtask):
- Conduct a comprehensive bias audit on training data
- Implement ongoing fairness monitoring across customer segments
- Develop bias-detection algorithms to run in parallel with recommendations
- Create a human review process for flagged recommendations
- Resources required (Comment): Data Science team (60 hours), QA team (40 hours), $10,000 for external bias audit.
- Contingency planning
- Trigger: Bias detection rate exceeds 5% in any customer segment during beta testing
- Contingency actions:
- Activate segment-specific recommendation filtering
- Deploy transparent explanations for AI decisions to affected customers
- Implement manual review override for affected segments
- Monitoring and review
- Review Frequency: Bi-weekly during beta, weekly post-launch
- Key Metrics: Bias detection rate, segment-specific satisfaction scores
- Last Review: March 18, 2025
- Status: In the Mitigation Planning Phase
In ProofHub, this entire risk would be captured as a task with subtasks for each mitigation and contingency action, custom fields for all parameters, and recurring review tasks.
An effective risk register is only valuable if its insights reach the right people in the right format. Senior management needs concise, actionable information. Their time is limited; their decisions are critical. Focus on the top 5-10 risks by score or category. Highlight significant changes since the last report—new high-priority risks, changing trends, or successfully mitigated threats. Emphasize required decisions and resource needs with clear recommendations.
Additionally, to ensure your risk register provides value beyond the project team, create role-based dashboards tailored to different stakeholders. Translate technical risks into business impact language that resonates with non-technical stakeholders. You can also include a one-page dashboard with key metrics that provide immediate situational awareness. Most importantly, provides a clear context for why each risk matters to the organization’s strategic objectives.
In ProofHub, you can:
- Utilize the form section to simplify risk entry and updates
- Create customized forms with guided fields for team members
- Set up role-based dashboards for different stakeholder needs
- Establish automated reporting with custom reports
- Use discussion boards for risk-related conversations
- Configure notification rules for critical changes
Best practices for creating and maintaining risk registers
Effective risk registers are the ones that evolve with your project. The fundamental difference between ceremonial risk management and effective risk management lies in the implementation approach. First, you need appropriate scaling. Not every project requires the same depth of analysis. Tailor your register’s complexity to the project’s size, criticality, and organizational culture. Secondly, standardized language across projects should be established to enable cross-project learning and resource optimization. Once your register is all set, here are some things that can help you reduce uncertainty and administrative burden:
- Establish clear ownership: Assign specific individuals responsible for each risk and the overall risk register maintenance. Ownership should be based on authority to take action, not just proximity to the risk.
- Regular reviews: Schedule periodic reviews (monthly, quarterly) to ensure the register remains current and accurate. These reviews should track risk trends and evaluate mitigation effectiveness.
- Consistent methodology: Use standardized criteria for risk assessment (probability, impact) across all projects and departments. Implement a consistent numbering system incorporating categories for instant recognition (e.g., FIN-001 for financial risks).
- Prioritization: Focus resources on the highest-impact risks based on a combination of likelihood and potential consequences. Include trend indicators (↑↓→) to show whether risks are increasing, decreasing, or stable over time.
- Integration: Embed risk management within regular business processes rather than treating it as a standalone exercise. Transform risk registers from mere documentation tools into communication hubs that connect stakeholders and drive decisions.
- Documentation: Record mitigation actions, deadlines, and results to build an organizational knowledge base. Use the “cause-risk-effect” format:
- “Due to [cause], [risk event] might occur, resulting in [consequence].”
- Stakeholder input: Gather perspectives from diverse team members to identify risks that might otherwise be overlooked. Create categories relevant to your specific project rather than using generic templates.
- Dynamic risk status management: Establish clear criteria for when risks should change status. Define specific escalation triggers (score increases, proximity decreases, failed mitigation) and de-escalation criteria (successful mitigation, external condition changes, impact reduction).
- Historical tracking: Document how risks evolve over time by logging status changes with dates and reasons. This historical record becomes invaluable for improving future risk management, as demonstrated by healthcare technology projects where pattern recognition saved millions in potential disruption costs.
- Residual risk assessment: Calculate residual risk after mitigation strategies are implemented to force an honest assessment of whether your strategies actually work or just create a false sense of security.
- Response strategy differentiation: Clearly distinguish between preventive actions (mitigation) and reactive plans (contingency), recognizing they serve different purposes and involve different resources.
Common pitfalls to avoid
Even well-intentioned risk management efforts can fall victim to predictable traps. The most insidious is the “check-box syndrome”—creating a risk register because methodology demands it, then ignoring it during actual project execution. Honestly, I have been guilty of this, too, and a few other mistakes that I have listed below:
- Static registers: Treating the risk register as a one-time document rather than a living tool that requires regular updates. Risk management is inherently dynamic and must evolve throughout the project lifecycle.
- Overwhelming detail: Including too many low-level risks that dilute focus from critical threats. This can lead to “risk register fatigue,” where important items get lost in the noise.
- Vague risk descriptions: Using ambiguous language that makes impacts difficult to quantify or address. Without specific descriptions, effective mitigation becomes nearly impossible.
- Neglecting positive risks: Focusing only on threats while ignoring potential opportunities. A comprehensive risk register should capture both negative and positive uncertainties.
- Siloed approach: Creating disconnected risk registers across departments without sharing insights. This prevents organizational learning and pattern recognition.
- Delayed updates: Failing to promptly document new risks as they emerge or update the status of existing risks. Timely updates are essential for effective risk response.
- Insufficient follow-through: Identifying risks but not implementing or tracking mitigation strategies. Without action and monitoring, the risk register becomes merely an academic exercise rather than a practical management tool.
- Missing knowledge transfer: Failing to record lessons learned when risks materialize or are successfully closed. These insights prevent recurring issues and build valuable institutional knowledge.
- Generic templates: Applying standard templates without customizing categories and approaches to fit the specific project context, reducing relevance and effectiveness.
Out of all these, perhaps most damaging is the “orphaned risk register”—where responsibility for maintenance is unclear, leading to gradual obsolescence. Effective risk management requires both discipline and pragmatism in equal measure.
Frequently asked questions
1. Who creates a project risk register?
For large or critical projects, a dedicated risk coordinator might manage the risk register. However, in most cases, the project manager shoulders this responsibility. Importantly, risk identification isn’t a solo task—it’s a collaborative effort. Every team member and stakeholder, including clients and sponsors, should contribute to identifying and assessing potential risks, as they might have unique insights unknown to the core project team.
2. How does a risk register fit into an organization’s overall risk management framework?
A risk register is one component of a comprehensive risk management framework. While the register focuses on identifying and tracking specific project risks, it should connect to enterprise-wide risk policies, governance structures, and reporting mechanisms. The most effective organizations integrate project-level risk registers with portfolio risk management and strategic risk considerations to create a cohesive approach that aligns with business objectives.
2. What’s the difference between risk management and crisis management?
Risk management is proactive and focuses on identifying, assessing, and mitigating potential threats before they materialize. Crisis management is reactive and deals with significant negative events that have already occurred. A robust risk register helps bridge these disciplines by identifying potential crises early and establishing contingency plans that can evolve into crisis response protocols if needed.
3. How do agile methodologies handle risk registers differently from traditional project management?
Agile approaches typically integrate risk management into regular ceremonies rather than maintaining a separate formal register. Risks are often captured as “blockers” or “impediments” in daily standups, with mitigation strategies discussed during sprint planning and retrospectives. However, for complex projects, many agile teams still maintain a simplified risk register that focuses on high-impact risks while keeping documentation lightweight and adaptable.
4. How can organizations balance thoroughness in risk management with avoiding excessive bureaucracy?
The key is proportionality—scaling your risk management approach to match your project’s complexity and criticality. For smaller projects, a streamlined register focusing on top 5-10 risks may be sufficient. For major initiatives, a more comprehensive approach is warranted. Technology solutions like ProofHub help reduce administrative burden while maintaining rigor by automating updates, generating reports, and facilitating collaboration around risk response.
5. What role does psychological safety play in effective risk management?
Psychological safety is crucial for honest risk identification and reporting. When team members fear blame or negative consequences for raising concerns, they’re less likely to report potential problems early. Organizations with strong risk cultures create environments where identifying risks is rewarded rather than punished, leading to earlier detection and more effective mitigation strategies.
7. How should organizations approach risk appetite and tolerance in their risk management strategy?
Risk appetite (the amount of risk an organization is willing to accept) and risk tolerance (the acceptable variation around specific objectives) should be explicitly defined and communicated. These parameters help teams determine which risks require mitigation versus which can be accepted. Different projects within the same organization may have different risk appetites based on their strategic importance, innovation requirements, and regulatory context.
Conclusion
Risk management is a dynamic field. The mastery of managing risks doesn’t require perfection from day one. Start by implementing just a few key practices mentioned above. I would recommend starting with the cause-risk-effect format, establishing clear ownership, and documenting how risks evolve.
For those ready to elevate their risk management, tools can be a powerful ally. You can either check out my companion article, “11 Top Risk Management Software Solutions for 2025,” or just get started with ProofHub‘s integrated risk management capabilities that many organizations have found to enhance their effectiveness significantly.